SysArmor
Next-Generation Intelligent Endpoint Intrusion Detection and Forensic Analysis System
System Demo
Intuitive overview of SysArmor's core capabilities
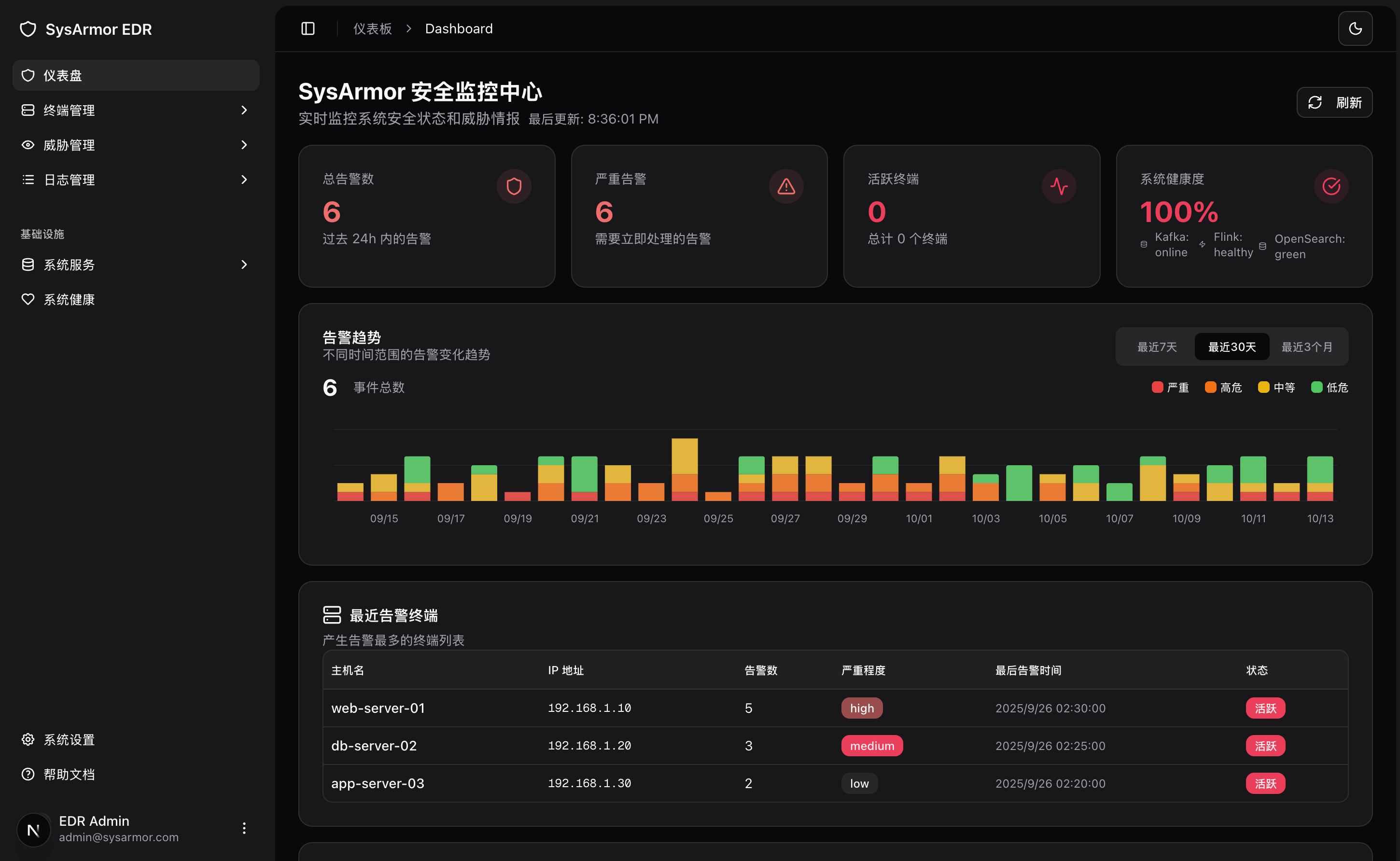
Data Dashboard
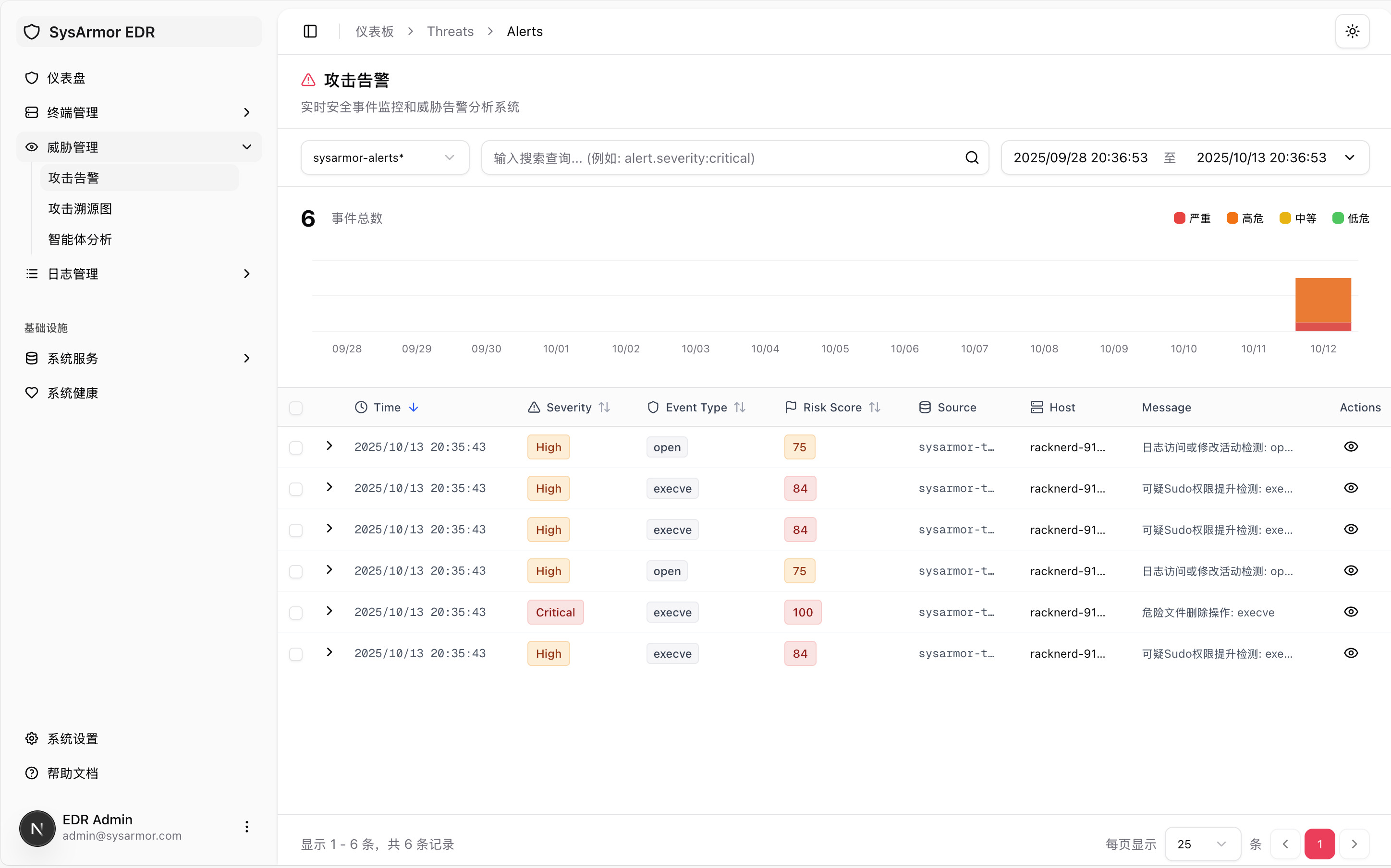
Threat Alerts
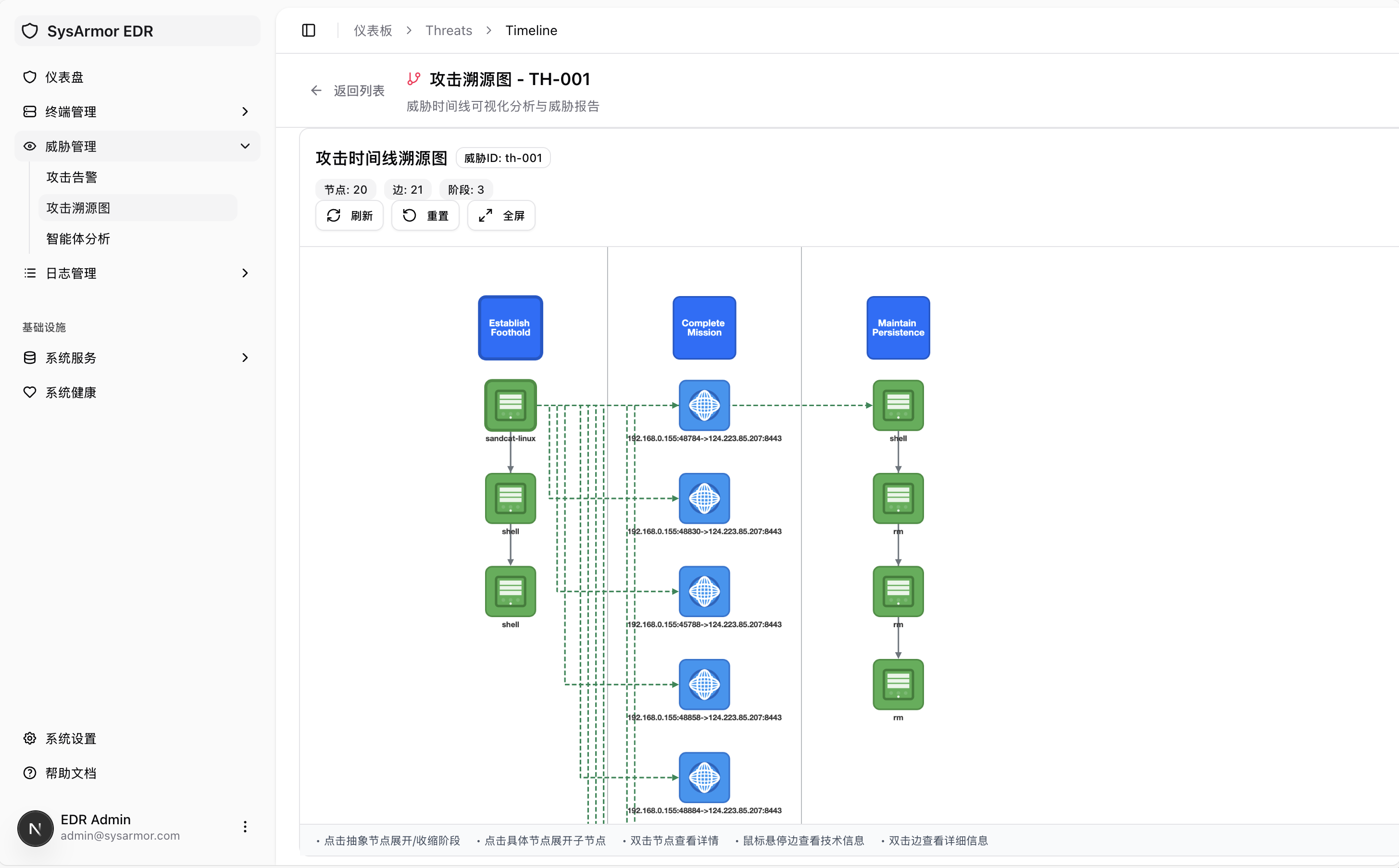
Forensic Analysis
System Architecture
Modular design and end-to-end data flow
graph LR
A[Collector] -->|Events| B[Middleware]
B -->|Stream| C[Processor]
C -->|Alerts| D[Indexer]
E[Manager] -.->|Manage| A
E -.->|Manage| B
E -.->|Manage| C
E -.->|Query| D
F[ML Services] -.->|Enhance| C
style A fill:#dbeafe,stroke:#3b82f6,stroke-width:3px
style B fill:#d1fae5,stroke:#10b981,stroke-width:3px
style C fill:#fef3c7,stroke:#f59e0b,stroke-width:3px
style D fill:#fecaca,stroke:#ef4444,stroke-width:3px
style E fill:#e9d5ff,stroke:#9f7aea,stroke-width:3px
style F fill:#fef3c7,stroke:#f59e0b,stroke-width:3px
Platform Infrastructure
Data Middleware
Vector + Kafka standardized data ingestion
Stream Processing
Flink real-time event transformation and detection
Index Storage
OpenSearch alert indexing and retrieval
Control Plane
Manager API unified orchestration
Web Interface
Alert visualization and operations management
Monitoring System
Prometheus system monitoring
Core Capabilities
Three technical breakthroughs through hardware-system-software co-design
Comprehensive Security Logs
Hardware-System Co-design
Achieves comprehensive and secure system log collection through hardware load
offloading and security resource isolation, ensuring log integrity and
security
• NoDrop: Multi-threaded secure
collection
• DPUaudit
Real-time High-precision Intelligent Detection
System-Software Co-design
Utilizes Steiner tree abstraction and threat intelligence knowledge base to
achieve comprehensive and accurate intelligent threat detection, ensuring
real-time and precise detection
• NodLink: First online
provenance detection system
• Order-of-magnitude accuracy
improvement
Significantly Improved Analysis Efficiency
Threat Semantic Understanding
Through threat level assessment and threat step understanding, combined with
real-time knowledge base and large language models, achieves semantic-level
threat behavior understanding based on attack lifecycle
• KnowHow: Attack behavior
understanding
• Natural language report
generation
Evolution Roadmap
Complete solution from Agentless to Agent + ML
v0.1.0 - Agentless Initial Release
- rsyslog/auditd zero-intrusion collection
- Kafka + Flink + OpenSearch streaming pipeline
- Compatible with sysdig/falco rule detection engine
v0.2.0+ - Agent + ML
- Policy distribution and automatic response
- NodLink anomaly alerts + KnowHow threat understanding
- Agent deep analysis
Unified Model
Agentless and Agent share data format and ingestion interfaces
Progressive Evolution
Smooth transition from rapid deployment to deep collection
Open Extension
Support for open-source components like Wazuh
Related Research Foundation
System security research achievements from PKU Computer Science OS Lab
NoDrop
USENIX Security 2023
Secure and trustworthy provenance log collection with multi-threaded architecture, achieving resource isolation based on threadlet
ProvWeb
IEEE TDSC 2023
Malicious website detection from system provenance perspective, achieving F1 Score of 93.7%~99.7%
NodLink
NDSS 2024
First online provenance detection system, achieving efficient and accurate real-time APT attack detection and investigation
KnowHow
NDSS 2026
Real-time and efficient APT attack behavior understanding and reasoning, based on attack lifecycle modeling
DPUaudit
HPCA 2025
DPU-assisted pull-based near-zero cost system auditing solution
RT-NoDrop
RTSS 2025
Predictable and secure system auditing solution for real-time systems
ProvAudit
IEEE TDSC 2025
Enhancing advanced privacy inference through system provenance data
Query Provenance Analysis
S&P 2025
Efficient and robust defense against query-based black-box attacks
PKU Computer Science Operating Systems Lab has long been engaged in operating system security research in ubiquitous computing environments, achieving breakthrough results in system provenance analysis, attack detection and protection, and AI system security. Learn more →